What Is Typosquatting? A Practical Guide to Identifying and Preventing Look-Alike Domains
24.12.2025
Contents
The Federal Bureau of Investigation reported $16.6 billion in direct financial losses from cybercrime in the U.S. in 2024. One of the threats contributing to this staggering number is typosquatting — a tactic often used for phishing, personal data breach, selling of counterfeit products, and many other fraudulent activities.
Look-alike domains quietly steal high-intent traffic, reduce revenue, and damage reputation. All while staying under the radar — the targeted brands are often completely unaware of someone posing as them to deceive users.
As a brand, the worst you can do is stay ignorant of red flag domains and allow someone to mislead customers and destroy the reputation you’ve worked so hard to build. Read this practical guide to find out how you can monitor and prevent attacks before they damage your brand.
What Is Typosquatting & How It Impacts Brands
Registering a domain that intentionally closely resembles a misspelled domain or brand name of a well-known company is called typosquatting. The fake websites hosted on those domains imitate or even completely copy the official company pages. This is a domain abuse tactic used by fraudsters and dishonest affiliates with the goal of misleading users to steal data or monetize high-intent traffic.
The attackers monetize in several ways:
- • Lead hijacking: Fraudulent affiliates and competitors use typosquatted domains to divert branded traffic, steal leads, and get undeserved commission payouts.
- • Ad fraud: Sometimes the real goal of fake domains is to run ads that look like legitimate brand creatives and push users toward unauthorized sellers or fraudulent storefronts.
- • Phishing: Fraudsters can practice URL phishing to steal user data, which is later resold or exploited for malicious activities.
- • Malware: Some fake domains distribute harmful software that steals sensitive data, uses the infected computers for cryptomining operations, or corrupts critical files.
The impact on brands:
- 1. Financial: According to FairWinds' analysis, typosquatting causes the 250 most highly trafficked U.S. websites to lose up to $327 million a year due to lost sales, unintended advertising and lost impressions. Taking legal action may cause them to lose another $79 million, bringing the total yearly loss to $406 million.
- 2. Reputational: The deceived customers blame the brand for the damage, believing that it’s the company's responsibility to stop impersonators and prevent fraudulent schemes. Not only that, but they’ll always be suspicious of the brand's marketing going forward, associating it with hidden cyberattacks.
- 3. Marketing: Since a part of branded traffic will be relocated towards look-alike domains, the marketing results will suffer from growing customer acquisition costs and failing conversion rates, while the cause will remain invisible.
The Range of Look-Alike Threats & How to Discern Them
URL squatting is an umbrella term covering all the practices involving the registration of look-alike domains. Here’s how the main techniques differ — and how to recognize them.
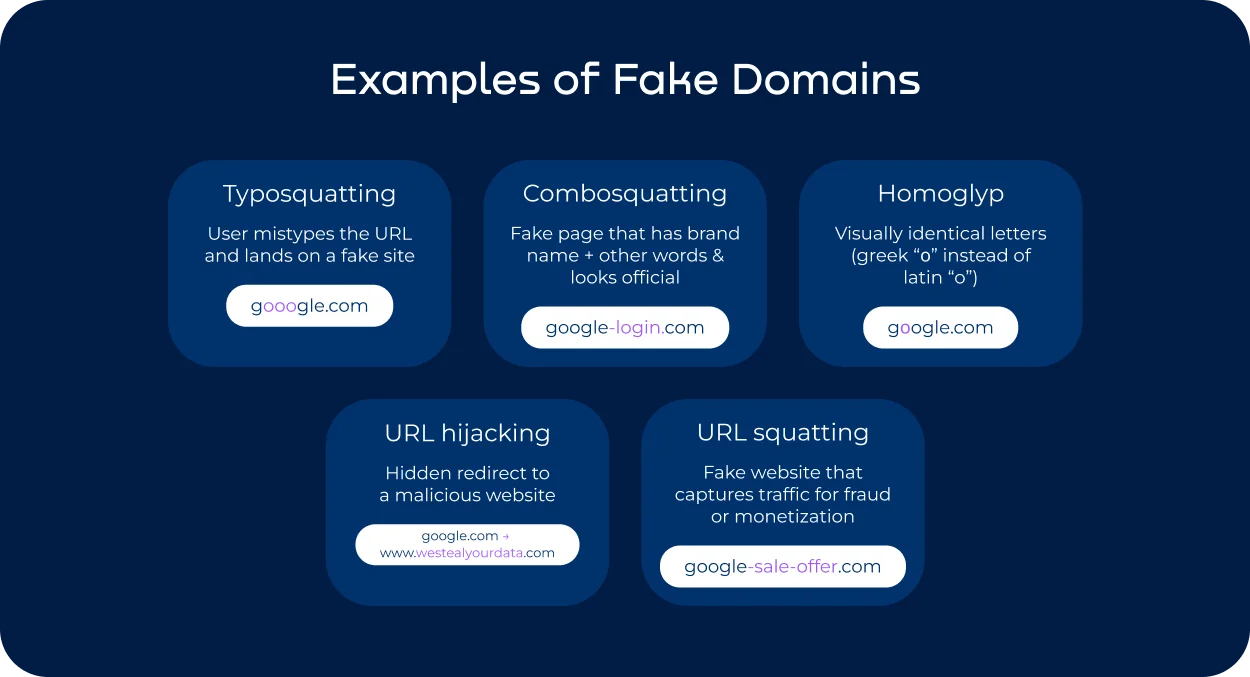
- • Typosquatting exploits misspellings, swapped letters, duplicated characters, and plural or singular variations.
- • Combosquatting uses a combination of a well-known domain or brand with extra words that make it appear plausible, often imitating service or account-related pages.
- • Homoglyph attack replaces letters with visually similar characters from other alphabets or symbol sets (e.g., Latin “o” → Cyrillic “о”), creating domains that look authentic at first glance.
- • Character insertion adds or subtly replaces a single character in a way users rarely notice, such as double letters or adjacent keyboard substitutions.
- • TLD switching, which involves registering the brand name under a different top-level domain (e.g., .net instead of .com).
Real-World Examples of Domain Abuse
The 2024 ThreatLabz Phishing Report shows the following use cases:
An Office 365 page got spoofed by subtly adding an extra character into the domain and turning office365 into offlice365. The fake website tricked users into entering their credentials to steal login information. After victims submitted the form, they were redirected to the legitimate page, making the deception harder to detect. Another case involved Microsoft OneDrive. The operators used combosquatting, registering a domain that could be used for a legitimate login page. The fake domain hosted a remote monitoring and management software often used for malicious purposes.
How Domain Abuse Evolved: Trends and Risks in 2026
According to the Phishing Landscape 2025 study by Interisle Consulting Group, the number of unique domain names reported for phishing rose to over 1.5 million, showing a 38% increase over the last year. This is the highest number in the last five years.
Another recent report by Vedere Labs shows that at least 10% of the domains registered in the period from December 2024 to June 2025 used typosquatting and impersonated known brands.
Domain fraud and black hat affiliate marketing are clearly on the rise — but how do fraudulent actors evolve their tactics so rapidly? The following trends hold the answers:
- 1. Surge in new TLDs. Their affordability and minimal verification requirements make newer TLDs ideal for look-alike domains. Users don’t usually remember the exact website address, making it easy to overlook a different domain extension — and imitators exploit that.
- 2. Automation and high-velocity domain generation. These days creating fake domains is easier than ever due to the rising number of available automation tools. Modern threat groups automate domain generation in bulk, producing hundreds or even thousands of variations. Research confirms this, showing that new domains appear in large-scale bursts: DomainTools observed 681,099 new domains in a single day on July 3, 2024 — about 19% of them were flagged as irregular.
- 3. Abuse probability scales with brand size and PPC spend. Larger brands — especially those with significant PPC budgets — face a higher probability of impersonation attempts. Strong brand recognition creates incentives for attackers: more search demand, more user trust, and more chances to intercept high-intent traffic.
How to Identify Typosquatting and URL Squatting

Here’s a checklist of signals that can help identify that your brand is under an ongoing attack:
- Sudden drops in branded conversions despite stable traffic or ad spend.
- Lower CTR on branded PPC campaigns, especially in specific GEOs or time windows.
- Unexpected spikes in “Direct” traffic from unfamiliar or low-quality sources.
- Rising customer support tickets mentioning strange URLs, failed logins, or “wrong website” confusion.
- Affiliate reports showing unexplained traffic surges or leads attributed to suspicious referrers.
- Unusual brand keyword patterns in auction insights, such as new competitors or volatile impression shares.
- Increased complaints about phishing emails or fake login pages, indicating malicious domains are circulating.
- Analytics inconsistencies, such as sessions with unusually high bounce rates or atypical browser or device profiles.
- Email deliverability issues, which may occur if look-alike domains attempt spoofing or phishing via similar addresses.
To run a basic manual check, start by entering common variations of your domain into a browser to see whether any look-alike versions are active:
- • Misspellings and swapped letters
- • Plural or singular variations
- • Extra characters and duplicates
- • Alternative TLDs
- • Homoglyph look-alikes using visually similar letters
- • Combosquatting candidates
However, this type of checking can only uncover obvious threats. Fraudsters register new variations in bulk, creating thousands of typosquatted or combosquatted variants within minutes. A manual check can’t capture the full scope of typosquatting attacks.
Brands with active PPC or affiliate channels need continuous, automated monitoring to detect the threats that human review simply can’t catch. Dedicated domain-protection tools — including platforms that reveal cloaking and analyze look-alike patterns — help identify high-risk domains before they start stealing traffic or conversions.
How to Prevent Typosquatting and Domain Abuse
Here’s what you can do to prevent URL squatting:
- • Defensive domain registrations: Registering domain variations before fraudsters get them — including common typos, alternative TLDs, and combosquatting patterns.
- • DNS monitoring: Unexpected DNS changes, new A-records, or sudden SSL issuance can signal the early stages of an ongoing attack. Monitoring these signals helps detect red-flag domains, before they begin running ads or redirecting traffic.
- • Trademark monitoring: Tracking unauthorized use of your brand name is critical. Tools like Bluepear help surface these high-risk incidents early, giving teams evidence for faster response.
- • Email & domain security protocols: SPF, DKIM, and DMARC prevent fraudsters from using your legitimate domain in phishing campaigns.
- • Ad & SERP monitoring tools: Platforms like Bluepear catch typosquatters as soon as they start promoting in PPC or SEO, making it possible to react before fraudsters siphon traffic or conversions.
Detecting Typosquatting in PPC and Affiliate Channels
Fraudsters and opportunistic affiliates create look-alike domains to capture traffic, leads, or conversions intended for your brand. The motives vary: some aim to divert paid clicks from your PPC campaigns, others try to intercept affiliate traffic and earn undeserved commissions, and some deploy fraudulent schemes to exploit your audience directly.
Fake domains made with the intention of stealing leads and diverting traffic require promotion. When making landing pages and running ads, malicious actors typically employ the following tactics to evade detection:
- • Time-based targeting: Attackers schedule their ads to appear only during specific hours, days, or campaign windows.
- • GEO-locked hijacking: Ads are restricted to specific geographic locations, so that users outside the targeted region never see the fraudulent content, making detection difficult.
- • Cloaking: Fraudulent web pages display different content to users coming from specific sources such as PPC ads or affiliate links, while hiding it from Google bots and manual checks.
Manual checks often miss these scenarios entirely, which is why PPC managers and affiliate managers don't notice domain abuse unless they employ automated monitoring tools. In this environment, spotting threats early is crucial. Brands need tools that can see through the disguises and detect red flag domains the moment they start affecting traffic and revenue — that’s where Bluepear comes in.
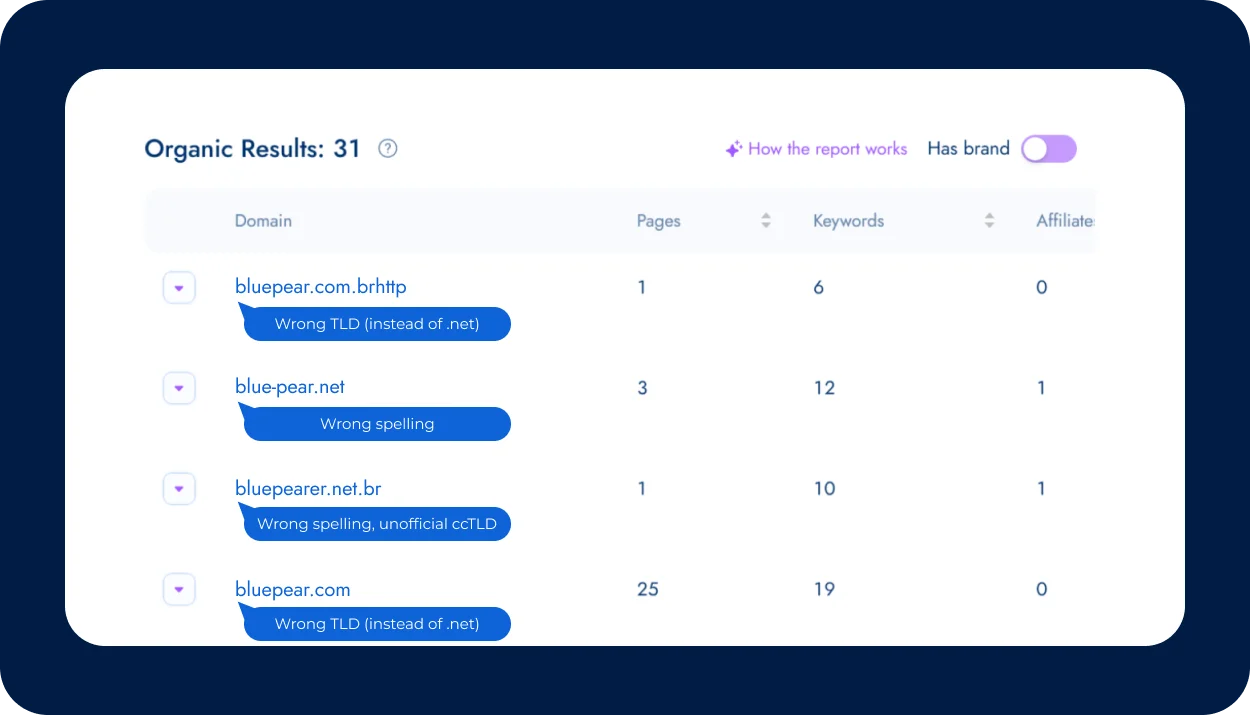
Bluepear continuously scans for any ads or sites using your brand name, no matter what tricks are being used to hide the activity. The tool surfaces potential threats that would otherwise go unnoticed — helping you stop revenue leakage and protect branded campaigns before the damage spreads. This kind of monitoring can immediately detect typosquatters running ads to steal conversions and mislead users. Try Bluepear now — it offers a free trial and transparent pricing, ensuring 24/7 brand protection.
Conclusion: Why Early Detection Matters
Typosquatting is no longer an occasional nuisance — it’s become a scalable, automated threat that directly impacts revenue and customer trust. As a result, the risks grow harder to spot without dedicated tools. A single missed look-alike domain can hijack branded traffic, distort analytics, or expose customers to phishing and malware. Early detection is the only way to stay ahead of fast-moving threats. For brands that rely on paid search, affiliates, or strong brand visibility, now is the time to audit your exposure and adopt automated monitoring. Bluepear helps reveal hidden PPC or affiliate abuse — giving teams the visibility they need to protect revenue and safeguard customer trust.
FAQ
How dangerous are look-alike domains for average users?
Quite dangerous. Look-alike domains often imitate official websites so closely that users fail to spot the difference. These domains may redirect to fraudulent storefronts, steal login credentials, install malware, or capture payment information.
How can brands check if they’re currently targeted?
A basic check includes reviewing typo variations, alternative TLDs, and suspicious redirects. However, manual reviews are unreliable due to the current scale of domain abuse and the cloaking techniques used by attackers. Brands running PPC or affiliate programs need continuous automated monitoring; platforms like Bluepear scan for red-flag domains linked to branded keywords in PPC campaigns or websites optimised for SEO.
What legal options exist for removing malicious domains?
Depending on the case, brands may pursue UDRP/URS actions, file abuse reports with registrars or hosting providers, or escalate through trademark enforcement channels. Evidence of phishing, impersonation, or URL hijacking strengthens the case. Automated monitoring tools help collect the necessary data for a faster takedown.
Which tools or monitoring methods work best for early detection?
The most effective methods combine large-scale scanning of new domain registrations, DNS and SSL monitoring, and PPC analysis for malicious redirects or cloaked ads. Bluepear integrates PPC and organic search monitoring into a single workflow, detecting look-alike domains the moment they begin monetizing via PPC or SEO.

